How to set up a WireGuard Site to Site VPN Between 2 EdgeRouters
Background
I’ve recently started college and I’m living in one of the dorms on campus. They provide 1 Ethernet jack per person per room. I have multiple wired devices, so at the very least I needed a switch, but I also wanted all the devices to be able to talk to everything back on my home network.
The best way to do this is with a site to site VPN. This lets devices on each end of the VPN tunnel communicate with each other as if they were directly on the same network.
My router of choice at home is an EdgeRouter Lite from Ubiquiti Networks. Originally I was going to use a Cisco Meraki MX64 firewall (get one for free here) at my dorm as my router, but the functionality is somewhat limited for my uses and I prefer the EdgeRouters, so I got a cheap EdgeRouter X off of eBay (college budget life) and went to work.
My original plan was to use OpenVPN because I’m familiar with it, but upon testing, I found the performance to be seriously lacking (up to about 7mbps). My dorm has 100/100 and home has 130/35, so that wasn’t going to cut it.
Plan B was IPSEC. Both EdgeRouters have hardware offloading for the encryption used in typical IPSEC configurations, so this seemed like a good high performance option. My next roadblock though was that I can’t port forward anything from my dorm, which made it difficult or impossible to establish an IPSEC tunnel. (may be possible but my Googling couldn’t find a way)
Finally, Plan C was to use WireGuard. I had made a post on Reddit with my IPSEC woes and it was suggested that I tried out WireGuard. WireGuard is a new type of VPN that aims to be fast, lightweight, and easy to set up (if you’re not me apparently), all while being highly secure. The details on how to set it up in on my hardware though were somewhat lacking, and it took quite a few hours to get it actually functional. My goal here today is to help someone else set up something similar without all the headache I went through, so without further delay, here’s how I did it.
My Setup
Here’s a quick and basic diagram of my setup, made using Creately.
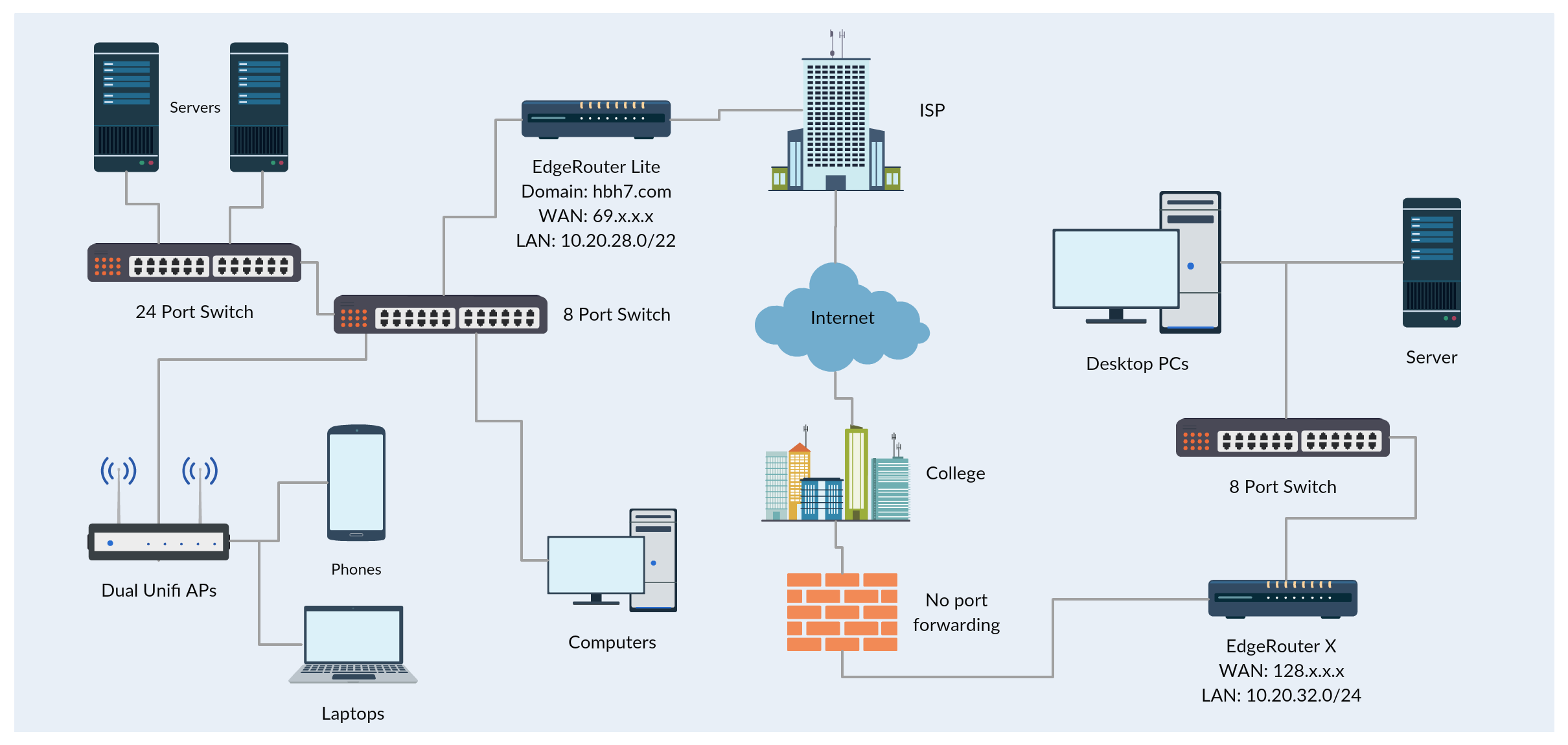
My Process
1. Install vyatta-wireguard on both routers. Find the download URL for your router and copy and paste it on line 3.
ssh <router ip>
sudo apt-get install wget (alternatively, use curl)
wget <download url, ex: https://github.com/Lochnair/vyatta-wireguard/releases/download/0.0.20180925-1/wireguard-e100-0.0.20180925-1.deb>
sudo dpkg -i <file name, ex: wireguard-e100-0.0.20180925-1.deb>2. Generate public and private keys on each router. Copy and paste the output into a text file for convenience. Top line of output is the private key, the bottom line is the public key.
wg genkey | tee /dev/tty | wg pubkey3. Configure the home router. I used 10.100.100.1 for the wireguard tunnel IP so that I could set up the allowed IPs as 10.0.0.0/8. It wouldn’t allow me to use 0.0.0.0/0 like I wanted, so this works out too since both subnets are on 10.x.x.x and 10.0.0.0/8 allows everything in that range.
configure
set interfaces wireguard wg0 address 10.100.100.1/24
set interfaces wireguard wg0 listen-port 51820
set interfaces wireguard wg0 route-allowed-ips true
set interfaces wireguard wg0 private-key <private key from this router from before>4. Configure the remote/dorm router. I used 10.100.100.2 for the wireguard tunnel IP on this one.
configure
set interfaces wireguard wg0 address 10.100.100.2/24
set interfaces wireguard wg0 listen-port 51820
set interfaces wireguard wg0 route-allowed-ips true
set interfaces wireguard wg0 private-key <private key from this router from before>5. Set up the other router (peer) on each router. Skip line 2 on the side with port forwarding (only useful on the side that can reach out to the other side with port forwarding), or run it on both sides if there is. Must be run on at least one side. Line 3 keeps the connection active so it works without port forwarding and doesn’t disconnect after a short while of no traffic.
set interfaces wireguard wg0 peer <other router's public key> allowed-ips 10.0.0.0/8
set interfaces wireguard wg0 peer <other router's public key> endpoint <public IP or domain name:port>
set interfaces wireguard wg0 peer <other router's public key> persistent-keepalive 15 6. Commit and save the changes on each router (otherwise they won’t take affect and be lost), then exit from configuration mode.
commit
save
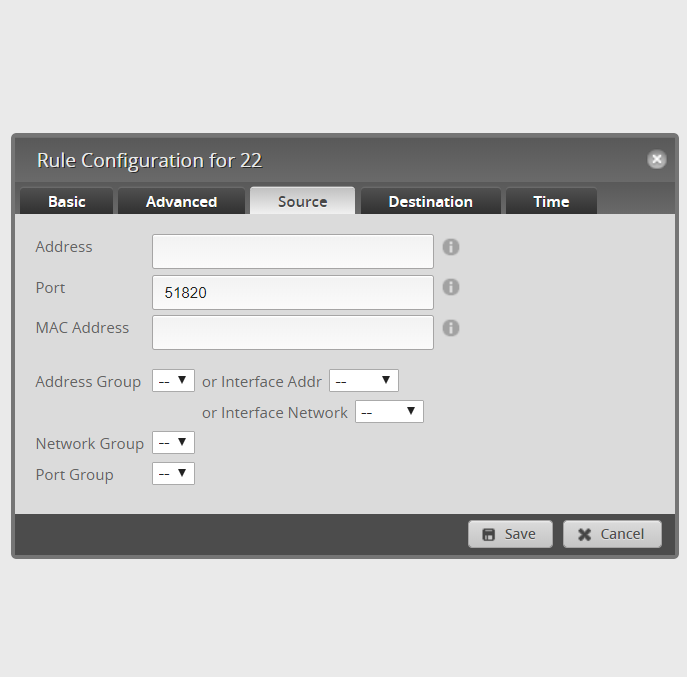
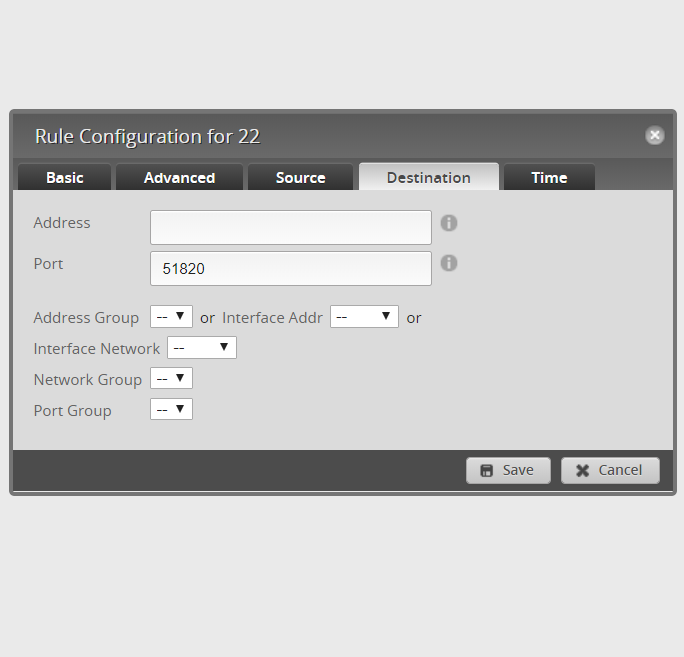
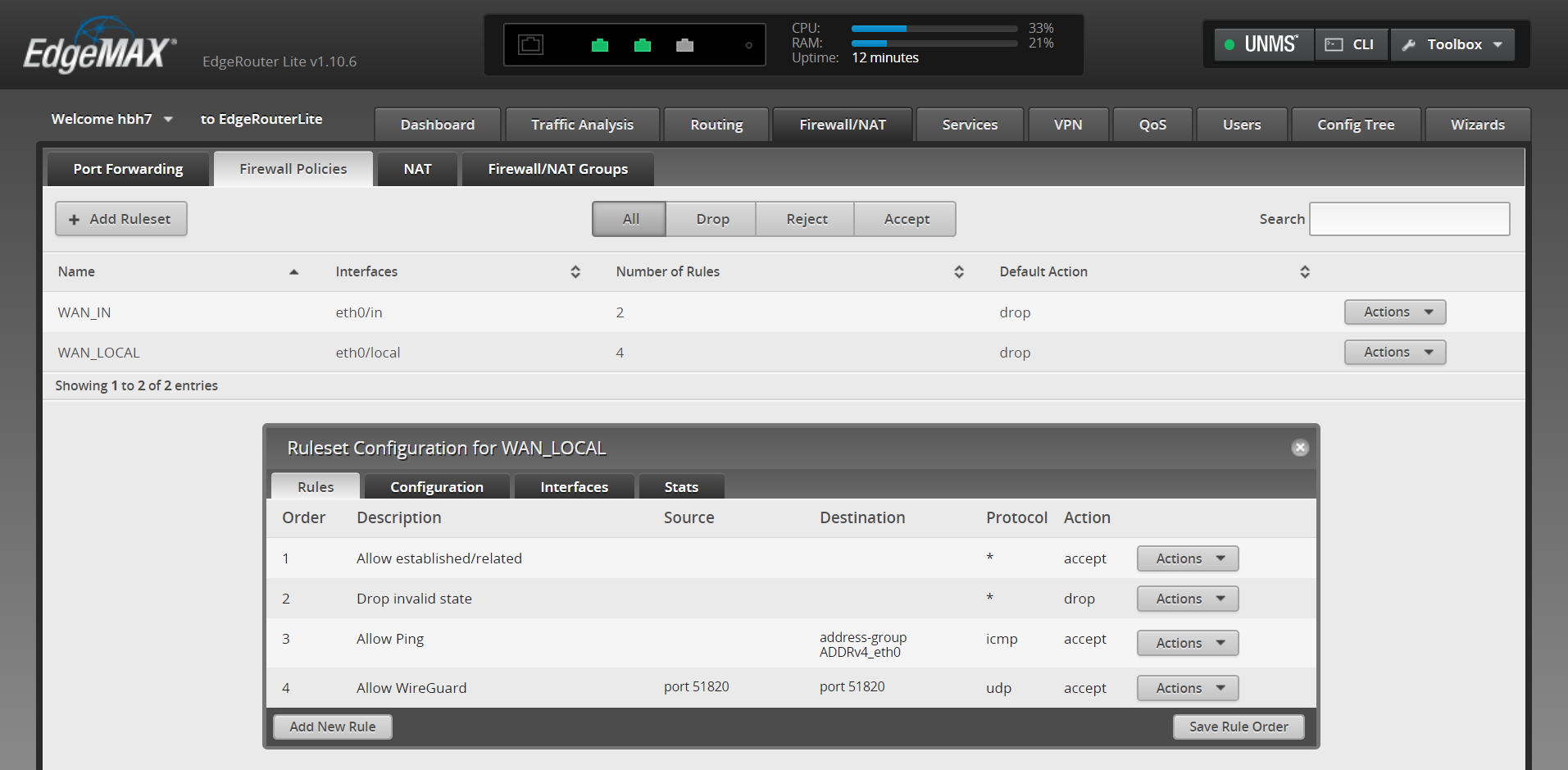
exit7. Go to the home router web UI, then Firewall/NAT -> Firewall Policies -> WAN_Local. Edit the ruleset configuration and add a new rule.
- Basic – Description: Allow WireGuard
- Basic – Action: Allow
- Basic – Protocol – UDP
- Source – Port: 51820
- Destination – Port: 51820
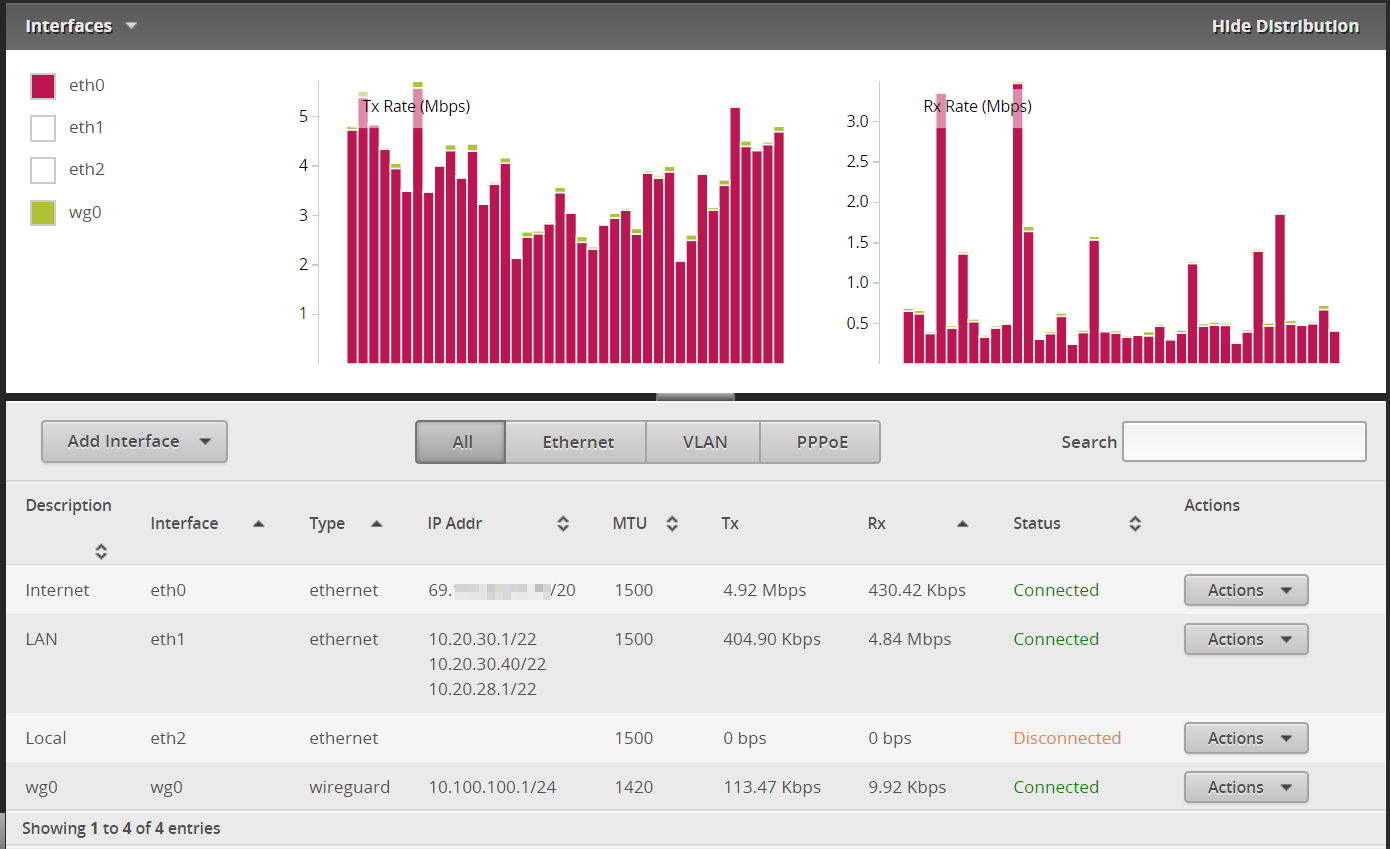
8. Theoretically, if everything worked, you should be able to see if there’s a connection.
sudo wgHome Router:
interface: wg0
public key: W6ap<home pubkey>
private key: (hidden)
listening port: 51820
peer: O8lz<dorm/remote pubkey>
endpoint: 128.x.x.x:51820
allowed ips: 10.0.0.0/8
transfer: 453.80 MiB received, 116.24 MiB sent
persistent keepalive: every 15 secondsDorm/Remote Router:
interface: wg0
public key: O8lz<dorm/remote pubkey>
private key: (hidden)
listening port: 51820
peer: W6ap<home pubkey>
endpoint: 69.x.x.x:51820
allowed ips: 10.0.0.0/8
latest handshake: 29 seconds ago
transfer: 120.42 MiB received, 453.46 MiB sent
persistent keepalive: every 15 seconds9. You should also see a new wg0 interface in the dashboard, possibly with traffic going over it already.
10. As a helpful commenter pointed out, you may need to add static routes if it doesn’t happen automatically for you. This is so that your routers know about the networks on the other end and can direct traffic accordingly. This should do the trick, on each end type this with the relevant info:
ip route add <subnet address>/<CIDR> dev wg0
Ex: ip route add 10.20.32.0>/24 dev wg011. Try pinging a device on the other end, from either end. If it comes back with a response, you should be all done!
hbh7@PC-at-dorm:~$ ping 10.20.31.101
PING 10.20.31.101 (10.20.31.101) 56(84) bytes of data.
64 bytes from 10.20.31.101: icmp_seq=1 ttl=62 time=16.7 ms
64 bytes from 10.20.31.101: icmp_seq=2 ttl=62 time=16.3 ms
64 bytes from 10.20.31.101: icmp_seq=3 ttl=62 time=15.9 ms
64 bytes from 10.20.31.101: icmp_seq=4 ttl=62 time=20.3 ms
^C
--- 10.20.31.101 ping statistics ---
4 packets transmitted, 4 received, 0% packet loss, time 3004ms
rtt min/avg/max/mdev = 15.960/17.343/20.318/1.746 msAssuming all went well, that should be it. Leave a comment below if anything is unclear, if you get stuck somewhere, or if something isn’t working right. Enjoy!
Helpful links I used
WIREGUARD ON EDGEOS FOR A FASTER HOME VPN
WireGuard VPN using an EdgeRouter X
Release: WireGuard for EdgeRouter
vyatta-wireguard
Site to Site VPN on a restricted network

Hi thanks for the tutorial!
Everything is working for me bar the final step… pinging!!
I lose all internet access once I start wireguard on the client!
Pinging works on the server side while it’s running however.
I’ve tried almost everything!
Hi, it sounds to me like you have some routing set up on the client side so that everything goes over the wireguard tunnel. Can you ping from the client to the server? Perhaps there’s also some firewall settings blocking the communication, although routing sounds more like it. If you share your config with a pastebin link, that may be helpful if you can’t see any source of the problem. Thanks for your comment!
hello , thanks for your article , but I have some questions.
here is my commands
on left site:
configure
set interfaces wireguard wg0 address 192.168.99.1/24
set interfaces wireguard wg0 listen-port 51820
set interfaces wireguard wg0 route-allowed-ips true
set interfaces wireguard wg0 private-key somesecret
set interfaces wireguard wg0 peer somesecret allowed-ips 192.168.99.0/16
set interfaces wireguard wg0 peer somesecret endpoint 111.111.111.111:51820
set interfaces wireguard wg0 peer somesecret persistent-keepalive 15
commit
and right site:
set interfaces wireguard wg0 address 192.168.99.2/24
set interfaces wireguard wg0 listen-port 51820
set interfaces wireguard wg0 route-allowed-ips true
set interfaces wireguard wg0 private-key somesecret
set interfaces wireguard wg0 peer somesecret allowed-ips 192.168.99.0/16
set interfaces wireguard wg0 peer somesecret endpoint 222.222.222.222:51280
set interfaces wireguard wg0 peer somesecret persistent-keepalive 15
if my lan were 192.168.1.0/24 and remote lan is 192.168.2.0/24
how do I change the allow ip ?
I firsy try to use allowed-ips 192.168.99.0/16 , but always comes after an error messages
and the same error with 192.168.0.0/8
Warning: AllowedIP has nonzero host part: 192.168.99.0/16
Warning: AllowedIP has nonzero host part: 192.168.0.0/8
then I can ping between routers(192.168.99.1 and 192.168.99.2) , but cant not ping clients behind the router ..
any suggestions ?? thanks !
I have to manually add static router in both routers
left site: ip route add 192.168.111.0/24 dev wg0
right site: ip route add 192.168.112.0/24 dev wg0
then the clients can ping to each other
Ah I bet you’re right about needing the static route. I can’t remember if mine was automatic or not but that could definitely make a difference. I’ll add that in. Thanks!
Hi there. So the reason you’re having issues with AllowedIP has nonzero host part seems to be with the /16 and /8 bits. So the way that would work is a /16 would give you 192.168.0.0-192.168.255.255 as addresses. I believe putting the 99 in there is upsetting it. This is the same issue with the /8, where that is 192.0.0.0-192.255.255.255. The 168 is upsetting it there. I think if you put in 192.168.0.0/16, you should be good to go.
Hi, Thanks for the instructions. I have 2 edgerouter X currently setup in this was between two sites. All seems to be working including Samba file shares across the wireguard interface. However I am unable to ping certain websites when the wg0 interface is enabled. If I disable it everything works fine. I think it may have something to do with the DNS but I cant figure it out. Any thoughts?
Nevermind, I had the wrong allowed IPs which was screwing it up.
Yeah the allowed IPs thing is peculiar and doesn’t always work as expected. Glad you figured it out and found my tutorial useful 🙂
Hey any chance you could do a tutorial on setting up a phone to use the edgerouter as a vpn server. I am trying to have it peer with my phone and can’t get it to work.
Probably not as I don’t actually run any EdgeRouters anymore, but I can try to offer a few pointers:
Make sure the VPN server port is port forwarded.
See where the process fails (no connection at all, connected but certain traffic doesn’t work, etc.).
If using OpenVPN, try WireGuard, or vice versa. If neither work then it’s probably not a protocol issue at least.
Hope this helps! You’re welcome to ask any other questions if you’d like and I’ll try to assist further.
Hi
Thanks for a great guide.
To all, rember when comming to:
set interfaces wireguard wg0 peer
needs to be put into single qoutes like ‘other router’s public key’
otherwise you can’t set allowed-ip and endpoint parameters.
BR
OFH
Hi Thanks for a great guide.
To all, rember when comming to: set interfaces wireguard wg0 peer public key
they need to be put into single qoutes
like ‘other router’s public key’
otherwise you can’t set allowed-ip and endpoint parameters.
BR OFH
If you have this config still, could you sanitize it and post it?
I’m trying to do this exact same thing and having no luck.
Thanks.
Hi,
Unfortunately I do not 🙁
Do you have any other questions I can try to answer? How far did you get?